WHAT IS THE US NATO TEMPEST
TEMPEST deals with radiated electromagnetic waves of equipment (both radiated and conducted) and assesses the eavesdropping risk.
All electrical and electronic equipment generates electromagnetic radiation (EMC). In EMC, radiation from data processing equipment, such as Laptops, Industrial Monitors or Military Touch Screen Displays, contains sensitive information that can be easily intercepted.
A receiver can interpret these signals undetected without direct access to the original device.
Tempest level
| Standard | Full | Intermediate | Tactical |
|---|---|---|---|
| NATO SDIP-27 | Level A | Level B | Level C |
| NATO AMSG | AMSG 720B | AMSG 788A | AMSG 784 |
| USA NSTISSAM | Level I | Level II | Level III |
| NATO Zones | Zone 0 | Zone 1 | Zone 2 |
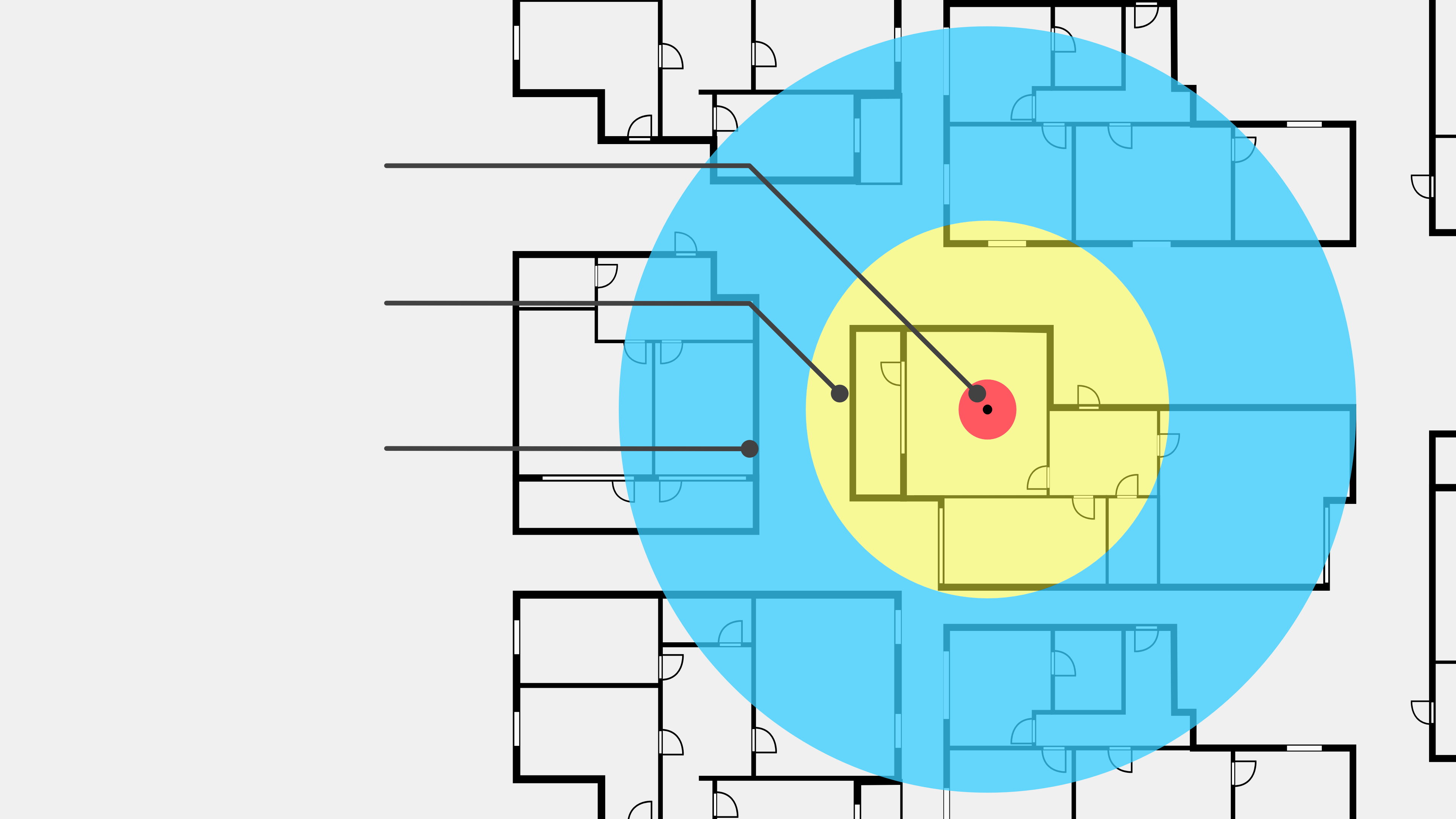
NATO Zoning
Defines an attenuation measurement method whereby individual rooms within a safety perimeter are classified as Zone 0, Zone 1, Zone 2, or Zone 3, and which requires a screening test standard for equipment handling secret data in these rooms.
Level A - NATO SDIP-27
Tempest level A is the strictest NATO standard and is therefore sometimes referred to as "FULL". Level A applies to environments and equipment where immediate eavesdropping can occur from the adjoining room (approximately 1 meter away). Therefore, this standard applies to equipment operated within NATO Zone 0.
Level B - NATO SDIP-27
Tempest Level B is the next highest NATO standard, also known as "IMMEDIATE". This standard applies to equipment that can not be heard from a distance of over 20 meters. This Tempest standard applies to equipment operating within NATO Zone 1. This standard protects equipment both from 20 meters of unobstructed distance and a comparable distance through walls and obstacles.
Level C - Nato SDIP-27
Tempest Level C is also referred to as "TACTICAL". This standard applies to environments and equipment within NATO Zone 2 (where eavesdroppers are assumed to be at least 100 meters away). This standard protects equipment from 100 meters of unobstructed distance or a comparable distance through walls and obstacles.
The term "TEMPEST" is a codename and acronym for a classified U.S. project that was used in the late 1960s to exploit and monitor electromagnetic radiation (EMR) and guard against exploitation. Today, the term has been officially replaced by EMSEC (Emissions Security), but it is still used by civilians online. The goal of the United States Information Assurance (IA) is to assure the availability, integrity, and confidentiality of information and information systems, including weapon systems, infrastructure management systems, and networks that are used to process, store, display, transmit, or protect Department of Defense (DOD) information.
Computing devices and other information systems are capable of leaking data in many peculiar ways.
As malicious entities increasingly target and attack core infrastructures, the IT security methods and policies for protecting highly sensitive and vulnerable locations have been evolving through the years.
Computer and network surveillance is the continuous effort to actively monitor the target device's activity, key actions and all data being uploaded to the hard drives. The monitoring process can be carried out by a single individual, criminal organizations, governments and large corporations, and is frequently done in a covert manner. Governments and large organizations currently possess an unprecedented ability to continuously monitor the activity of all internet users and citizens.
A shield puts an impedance (the effective resistance of an electric circuit or component to alternating current, arising from the combined effects of ohmic resistance and reactance) discontinuity in the path of a propagating radiated electromagnetic wave, reflecting it and/or absorbing it. This is conceptually very similar to the way in which filters work – they put an impedance discontinuity in the path of an unwanted conducted signal. The greater the impedance ratio, the greater the shield effectiveness (SE).
NATO countries have published lists of accredited testing labs and equipment that has passed the required tests. The Canadian Industrialtempest Program, the BSI German Zoned Products List, the UK CESG Directory of InfoSec Assured Products, and the NSAtempest Certification Program are examples of these lists and facilities. The certification must apply to the entire information system or device, not just several individual components, as connecting a single unshielded component could significantly alter the system RF characteristics.
The computer systems of various industries, governments, and people are susceptible to cyber-attacks, with the biggest targets being financial institutions, websites, apps, and micro-financial structures. Computer systems are also employed throughout telecommunication companies, water and gas systems, and nuclear power plants, making them vulnerable to attack. Personal and home devices, large corporations, medical records, and vehicles are also common targets, with some attacks aimed at financial gain and others aimed at crippling the company. The Internet of things (IoT) is being developed without appropriate consideration of the security challenges involved, and as the IoT spreads, cyber-attacks are likely to become an increasingly physical threat.
TEMPEST isn’t just an esoteric field of espionage that only the upper echelon military branches can use. A rather frivolous program known as “TEMPEST for Eliza” can be used by almost anyone at the comfort of their homes. TEMPEST for Eliza is a quick Linux hack that plays music over the radio of your choosing by displaying alternating black and white pixels on your monitor at just the right frequency. This plays music for the feds pointing their TEMPEST-sniffer antenna at your monitor. If you’re not currently being spied on, you can play the music for yourself using a handheld AM radio.
The red/black principle, also known as red/black architecture or red/black engineering, is a cryptographic principle that separates signals that contain sensitive or classified plain-text information from those that carry encrypted information. Alltempest standards require a strict "RED/BLACK separation or the installation of shielding agents with satisfactory SE, between all circuits and equipment which transmit classified and non-classified data." The manufacture oftempest-approved equipment must be done under careful quality control to ensure that additional units are built exactly the same as the units that were tested, as changing even a single wire can invalidate the tests.
Monitoring computers or similar information systems from a distance is possible by detecting, capturing and deciphering the radiation emitted by the cathode-ray-tube (CRT) monitor.
This fairly unfamiliar form of long-distance computer surveillance is known as TEMPEST, and involves reading electromagnetic emanations from computing devices, which can be hundreds of meters away, and extracting information that is later deciphered in order to reconstruct intelligible data.
We offer a variety of special materials and technical refinements for EMC-resistant touchscreen solutions – precisely adapted to your requirements and the area of application. Customer-specific special solutions are our strength.

Military applications pose a major challenge for the integration of touchscreens. A touchscreen for military applications must withstand extreme conditions, function highly reliably and comply with all EMC specifications.
EMC shielding does not always have to be expensive. We would be happy to develop efficient solutions for you in accordance with the specifications of the relevant standard. We have access to a large portfolio of implemented projects and already offer you many standard solutions without further development effort. Special shielding materials are in stock in our warehouse.


Increasing civilian demand
Within the armed forces, Tempest certified equipment is necessary to ensure protection against espionage.
Increasingly high levels of industrial espionage are making Tempest solutions relevant in the private sector as well.
Growing civilian demand shows that more and more companies are recognizing the threats and risks of the modern information society.
Impactinator® IK10 glass offers unparalleled impact resistance, making it a superior choice for applications requiring exceptional durability. This innovative family of special glasses has revolutionized the industry, enabling glass solutions previously deemed impossible.
Designed for touchscreen and protective glass applications, Impactinator® glass meets the stringent safety and vandalism standards of EN/IEC62262 IK10 and IK11. It excels in situations where impact resistance, weight reduction, image quality, and reliability are critical.
Choose Impactinator® glass for robust and dependable performance in demanding environments. Experience the future of glass technology with our cutting-edge solutions that ensure maximum protection and efficiency.