Monitoring from a Distance Monitoring from a Distance
Monitoring computers or similar information systems from a distance is possible by detecting, capturing and deciphering the radiation emitted by the cathode-ray-tube (CRT) monitor.
This fairly unfamiliar form of long-distance computer surveillance is known as TEMPEST, and involves reading electromagnetic emanations from computing devices, which can be hundreds of meters away, and extracting information that is later deciphered in order to reconstruct intelligible data.
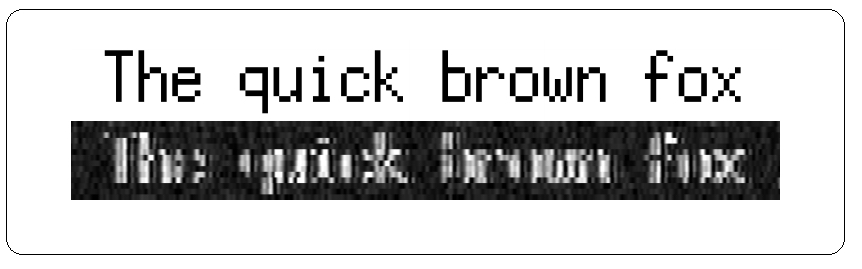
The text displayed on Fig.1 shows a cathode-ray tube monitor (top image) and the signal seen by a TEMPEST eavesdropper (bottom image).
Similar to TEMPEST, law enforcement agencies across Canada, the United States and in the United Kingdom use devices known as “StingRays” which are IMSI-catchers with both passive (digital analyzer) and active (cell-site simulator) capabilities. When operating in active mode, the devices mimic a wireless carrier cell tower in order to force all nearby mobile phones and other cellular data devices to connect to them.
In 2015, lawmakers in California passed the Electronic Communications Privacy Act which prohibits any investigative personnel in the state to force businesses to hand over digital communication without a warrant.
Additional to reading electromagnetic emanations, IBM researchers have discovered that the individual keys on a computer keyboard, for most devices, produce a slightly different sound when pressed, which can be deciphered under the right conditions with the help of a highly sophisticated machine. Unlike the keylogging software/malware which has to be installed on the computer to record the keystrokes of a keyboard, this type of acoustical spying can be done covertly from a distance. A simple PC microphone can be used for short distances up to 1 meter and a parabolic microphone is used for long-distance eavesdropping.
The average user types about 300 characters per minute, leaving enough time for a computer to isolate the sounds of each individual keystroke and categorize the letters based upon the statistical characteristics of English text. For example, the letters "th" will occur together more frequently than "tj," and the word "yet" is far more common than "yrg."
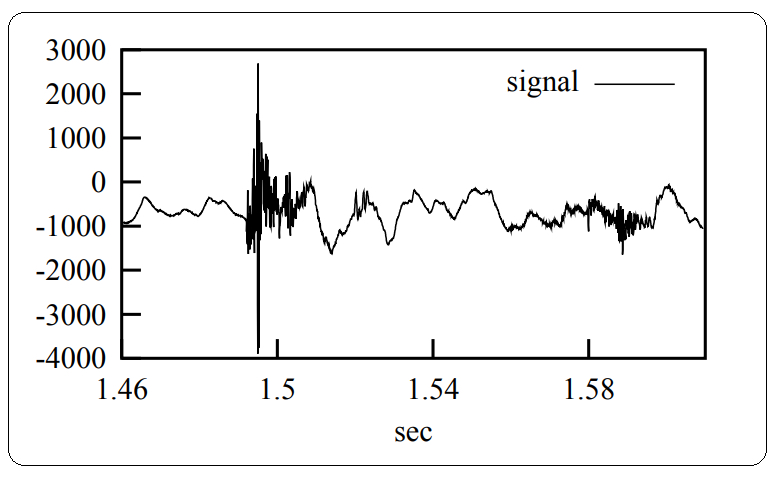
Fig.2 represents the acoustic signal of an individual keyboard click and the requisite time for the sound to fade away.
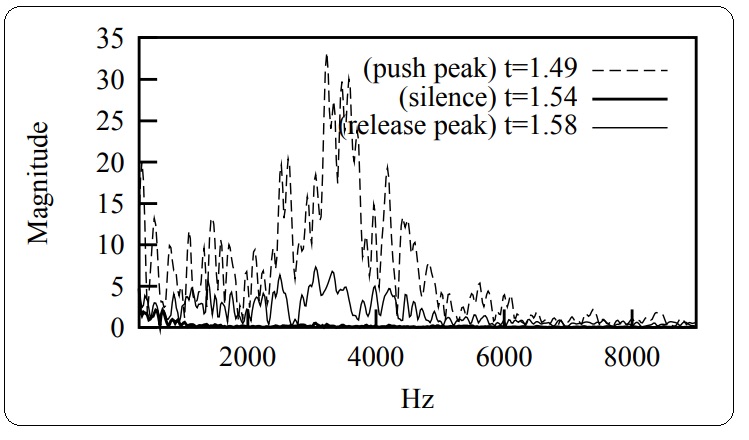
Fig.3 depicts the same acoustic signal as Fig.2 but it shows all the frequency spectrums corresponding to the “push peak” (the keyboard button being fully pressed), “silence” (the infinitesimal pause before keyboard the button is released) and “release peak” (the keyboard button being fully released).
| Keyboard A, ADCS: 1.99 | ||||||
|---|---|---|---|---|---|---|
| key pressed | q | w | e | r | t | y |
| recognized | 9,0,0 | 9,1,0 | 1,1,1 | 8,1,0 | 10,0,0 | 7,1,0 |
| key pressed | u | i | o | a | s | |
| recognized | 7,0,2 | 8,1,0 | 4,4,1 | 9,1,0 | 6,0,0 | 9,0,0 |
| key pressed | d | f | g | h | j | k |
| recognized | 8,1,0 | 2,1,1 | 9,1,0 | 8,1,0 | 8,0,0 | 8,0,0 |
| key pressed | l | ; | z | x | c | v |
| recognized | 9,1,0 | 10,0,0 | 9,1,0 | 10,0,0 | 10,0,0 | 9,0,1 |
| key pressed | b | n | m | , | . | / |
| recognized | 10,0,0 | 9,1,0 | 9,1,0 | 6,1,0 | 8,1,0 | 8,1,0 |
Fig. 4 shows each QWERTY keyboard key and its three accompanying sequential backpropagation neural network values. These values are created using a highly sensitive simulator program that is able to capture a wide range of sound frequencies, simplify and label the frequencies from 1 to 10, and most importantly - reconstruct intelligible data.
Acoustic emanations from keyboard-like input devices can be used to recognize the content being typed. It’s self-evident that a sound-free (non-mechanical) keyboard is an adequate countermeasure for this type of eavesdropping attack.
